(1)_2.jpg)
_2.jpg)
Placements Companies
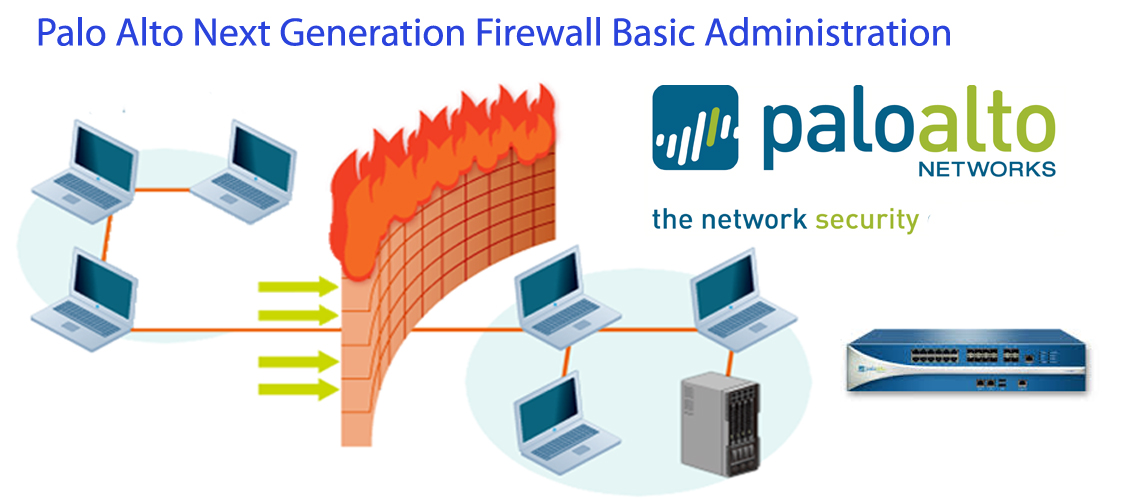
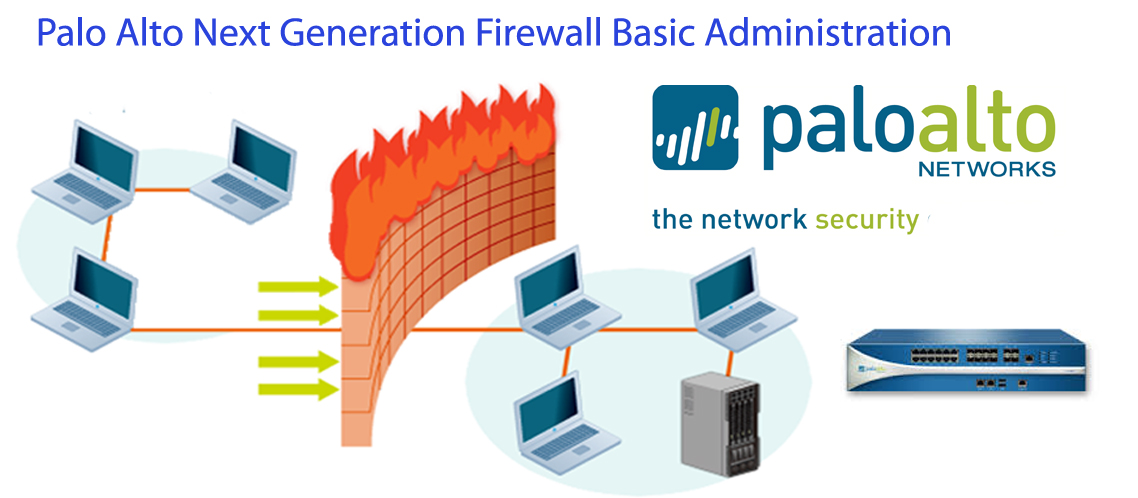
Palo Alto training will enable you to control, analyse and prevent cyber-attacks. In the modern day, security is the main concern and it is vital that we prevent our network from the cyber threats. Palo Alto's firewall range offers the organizations with the latest inspection technology and with the help of this the training organizations; one can prevent legacy and day-zero attacks. As the first line of response for any organization against a cyber-security attack, it is very important to comprehend the technology. There is the very wide and bright scope of this technology
Hence, it has become the best training providers among the rest. Our Academy program works with colleges and instructors to provide students with the necessary knowledge of next-generation cyber security to productively navigate today's rapidly changing cyber threat landscape. Our well trusted Palo Alto training gives the knowledge and one can easily secure the network and safely enable applications. REXTON IT SOLUTIONS offers a full portfolio of Instructor Led and e-Learning options. Together with our Authorized Training Centres (ATCs), our Instructor-Led classes feature the lecture and hands-on labs and are available through classroom instruction
Authorized Palo Alto Networks training from REXTON IT SOLUTIONS provides the next-generation firewall knowledge to you. You can now secure your network and safely enable applications without fear of security breaching. In our courses here in REXTON IT SOLUTIONS that feature the lecture and hands-on labs, you will learn to install, configure, manage and troubleshoot Palo Alto Networks firewalls. You will be given the skills and expertise needed to protect your organization from the most advanced modern day cyber security attacks.
You can be on the quick way of being the firewall expert after the training of our convenient delivery formats, including the classrooms. Labs infrastructure is advanced, well managed and you can access LAB 24X7 from anywhere and this training program will provide the 100 percent growth to your career
Rexton IT Solutions PaloAlto institute provides online training and classroom training. You can learn PaloAlto online and PaloAlto Course Offline. PaloAlto institute in Noida give you a better career and growth. Rexton PaloAlto training institute provides good lab setup for PaloAlto course. There are numerous PaloAlto certification and online training courses available to help you prepare for the PaloAlto exam. PaloAlto online course is created to help you pass the PaloAlto exam. While attaining PaloAlto certification confirms that you have the necessary training, expertise, knowledge, and devotion. PaloAlto course online is very easy. We are providing PaloAlto course online if you wants a good career in PaloAlto. In PaloAlto training Institute in Noida, you will work in the live programs which are the same as the real industry. Our PaloAlto class online is Instructor Led Training and Rexton is a best PaloAlto institute Noida. PaloAlto training institute provides 100% job if you lean PaloAlto course.


| Exam | Recommended Training |
|---|---|
| PCNSA | Palo Alto Certified Network Security Administrator - PCNSA_1 |
Module 1 – Platforms and Architecture
• Single Pass Architecture
• Control Plane and Data Plane
Module 2 – Administration & Management
• GUI, CLI, and API
• Config Management
• PAN-OS & Software Update
Module 3 – Interface Configuration
• Virtual Wire
• Tap
• Sub interfaces
• Security Zones
Module 4 – Layer 3 Configurations
• Interface Management
• Service Routes
• DHCP
• Virtual Routers
• IPv6 Overview
Module 5- Security Policy
• App-ID Process
• Policy Administration
• Policy Objects
• Defining Security Policy & Security Policy Configuration
• DMZ
Module 6- NAT
• Source and Destination NAT
• NAT Policy Configuration
Module 7 - Authentication Profiles
• Setting Up Authentication Profiles
• Creating a Local User Database
• Configuring RADIUS Server Settings
• Configuring LDAP Server Settings
• Configuring Kerberos Settings
Module 8 – User-ID
• User-ID Agent
• Enumerating Users
• Mapping Users to IP
• Users in Security Policy
Module 9 – VPN
• Virtual Private Networks - Intro
• VPN Tunnels
• IPSec and IKE
• IPSec and IKE Crypto Profiles
• Setting Up IPSec VPNs
• Defining IKE Gateways
• Setting Up IPSec Tunnels
• Defining IKE Crypto Profiles
• Defining IPSec Crypto Profiles
• Viewing IPSec Tunnel Status on the Firewall .
Module 10 – Reports and Logs
• Logging Configuration
• Scheduling Log Exports
• Defining Configuration Log Settings
• Defining System Log Settings
• Defining HIP Match Log Settings
• Defining Alarm Log Settings
• Managing Log Settings
• Configuring Syslog Servers
• Custom Syslog Field Descriptions.




_4.jpg)
_3.jpg)
(1).jpg)